2024 Q1 Management review
Date |
2024-05-21 |
|
Time |
13:00 |
|
Attendance |
Marin Božić |
President |
Luka Ferlež |
CTO |
|
Maja Pilipović |
LIA PM |
|
Tea Miličević |
AFBIS PM |
|
Hana Ercegovac |
Brisk PM |
Agenda
-
Privacy compliance review
-
Privacy policy review
-
Processing capacity review
-
PII use review
-
Cybersecurity review
Meeting minutes
Privacy & PII
-
Reviewed privacy policy as defined in contracts with clients
-
Reviewed & confirmed data use and storage policy
-
Reviewed per system privacy compliance
-
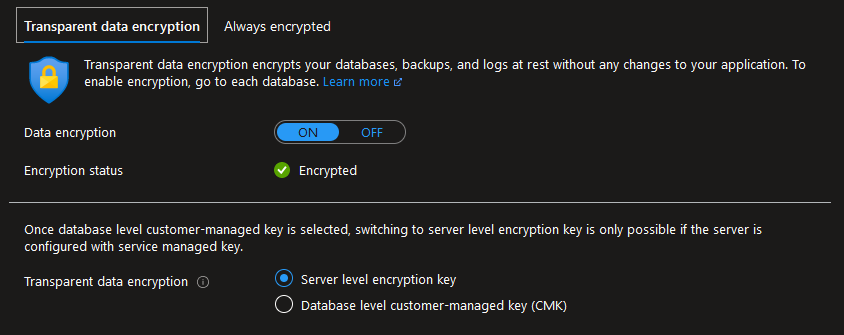
Reviewed LIA data encryption in place
 Figure 1. Data encryption
Figure 1. Data encryption -
Reviewed AFBIS data encryption in place
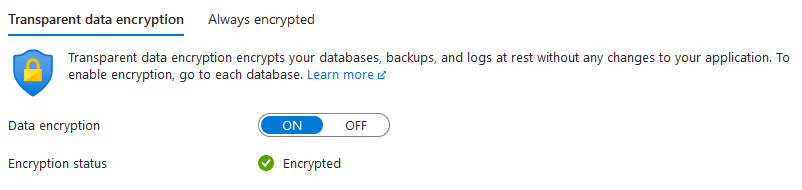 Figure 2. Data encryption
Figure 2. Data encryption -
Reviewed Brisk data encryption in place
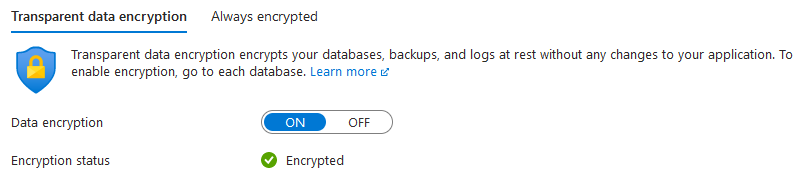 Figure 3. Data encryption
Figure 3. Data encryption -
Reviewed LIA data masking of PII
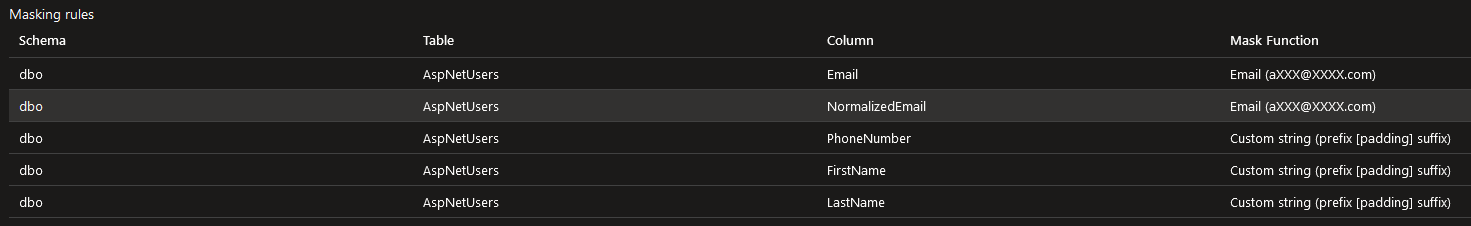 Figure 4. Identity data mask
Figure 4. Identity data mask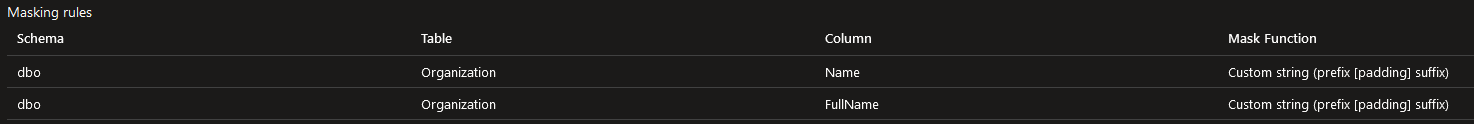 Figure 5. Organization data mask
Figure 5. Organization data mask Figure 6. Insurance data mask
Figure 6. Insurance data mask -
Reviewed AFBIS data masking of PII
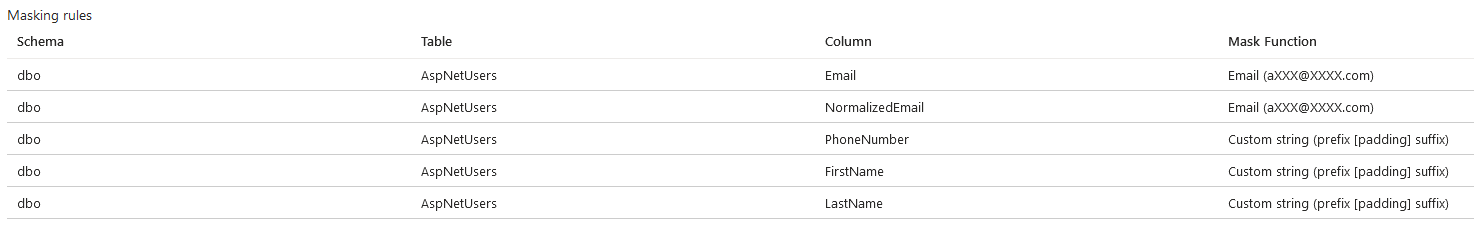 Figure 7. Identity data mask
Figure 7. Identity data mask Figure 8. Quoter data mask
Figure 8. Quoter data mask -
Reviewed Brisk data masking of PII
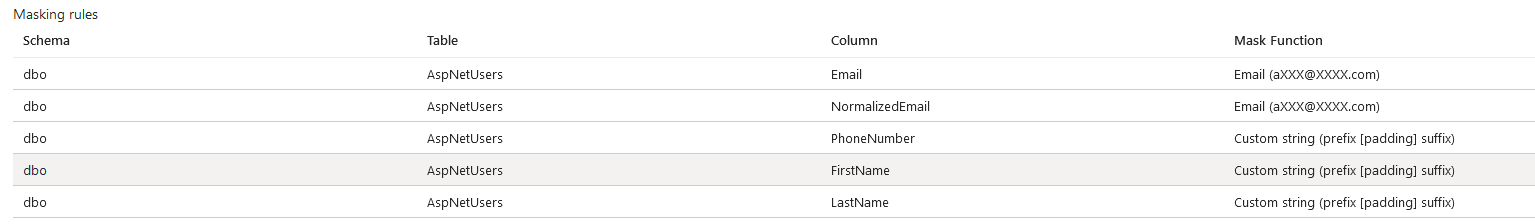 Figure 9. Identity data mask
Figure 9. Identity data mask Figure 10. Quoter data mask
Figure 10. Quoter data mask
Processing capacity review
-
Reviewed LIA processing capacity
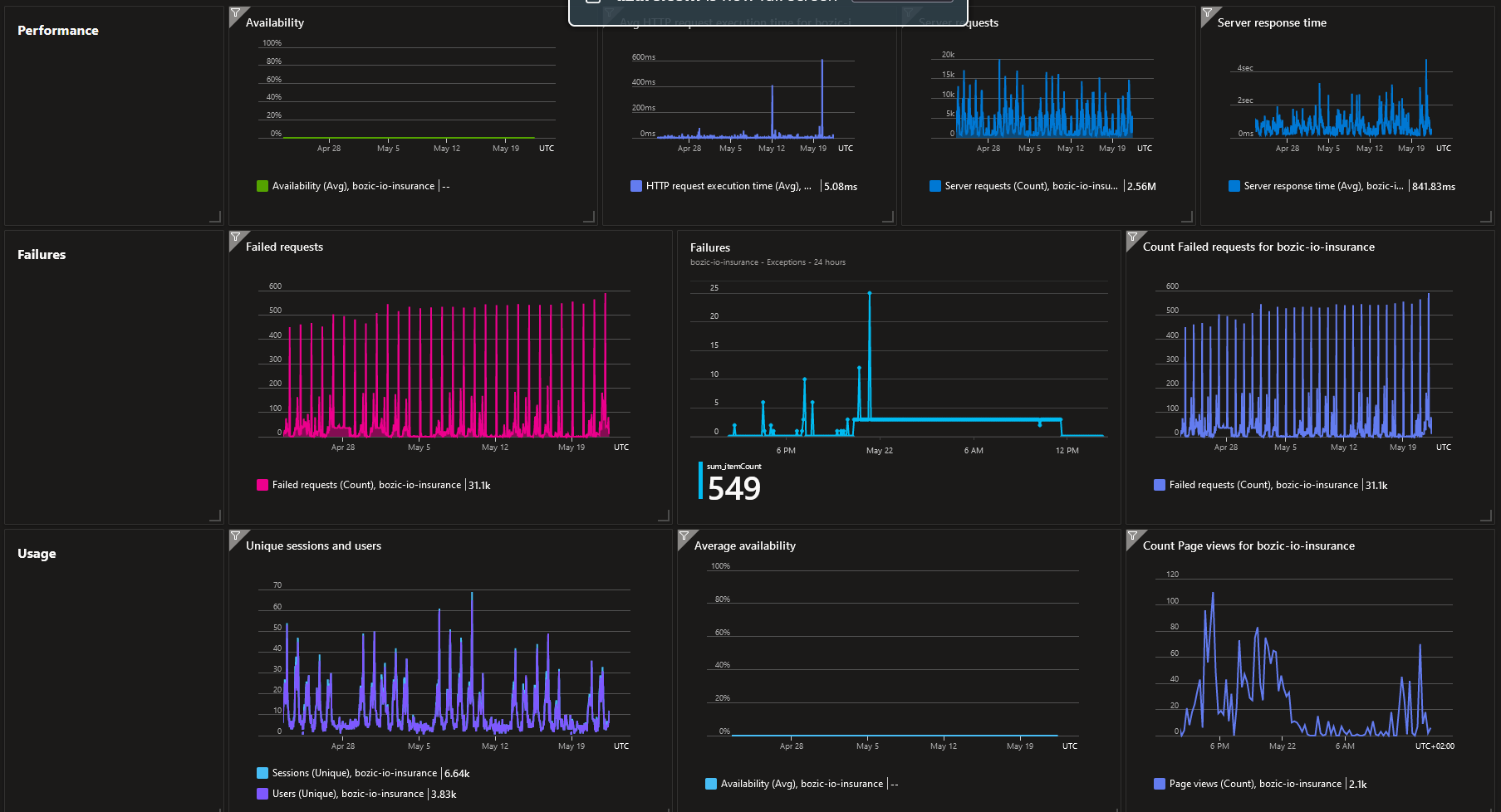 Figure 11. LIA processing capacity
Figure 11. LIA processing capacity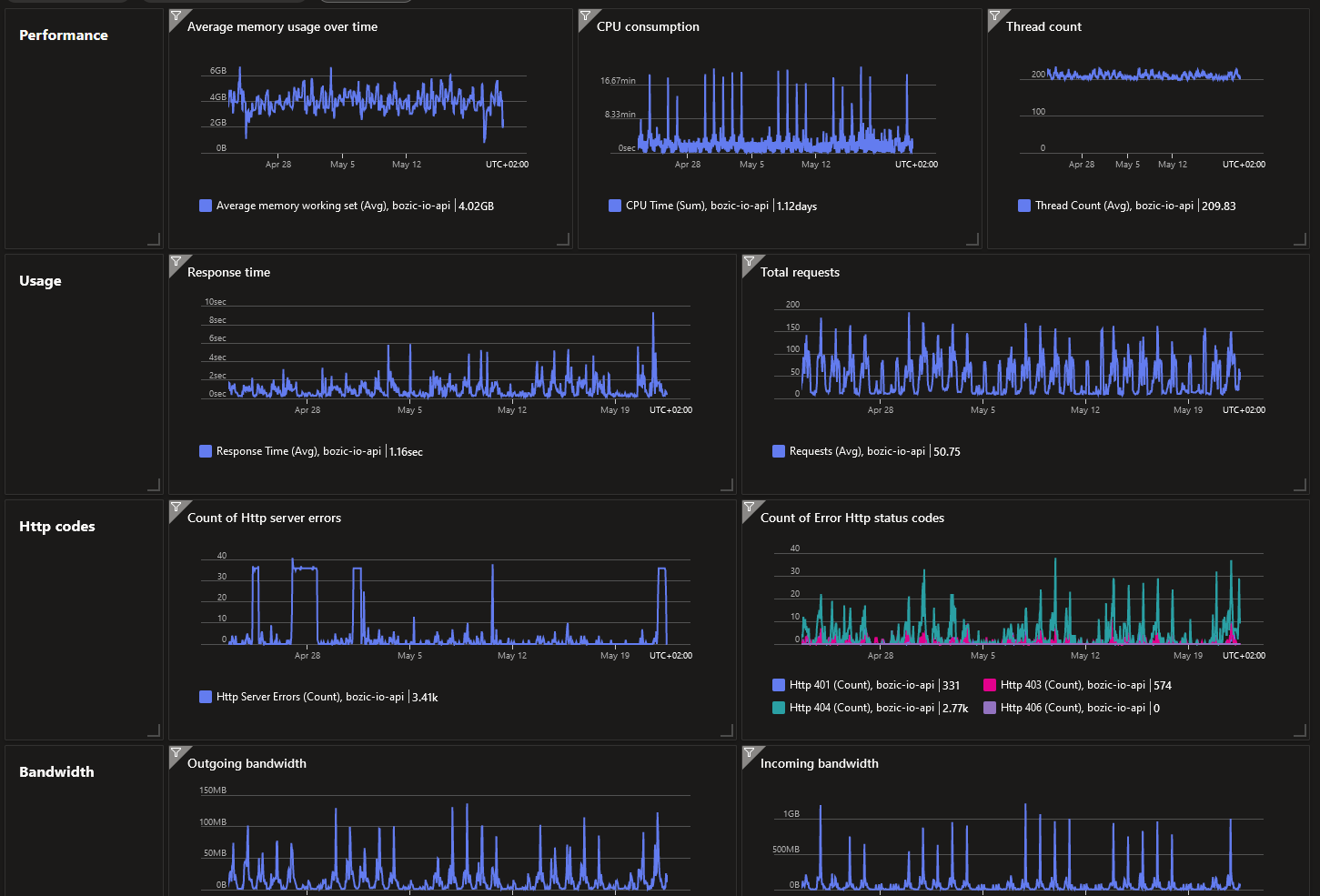 Figure 12. LIA API processing capacity
Figure 12. LIA API processing capacity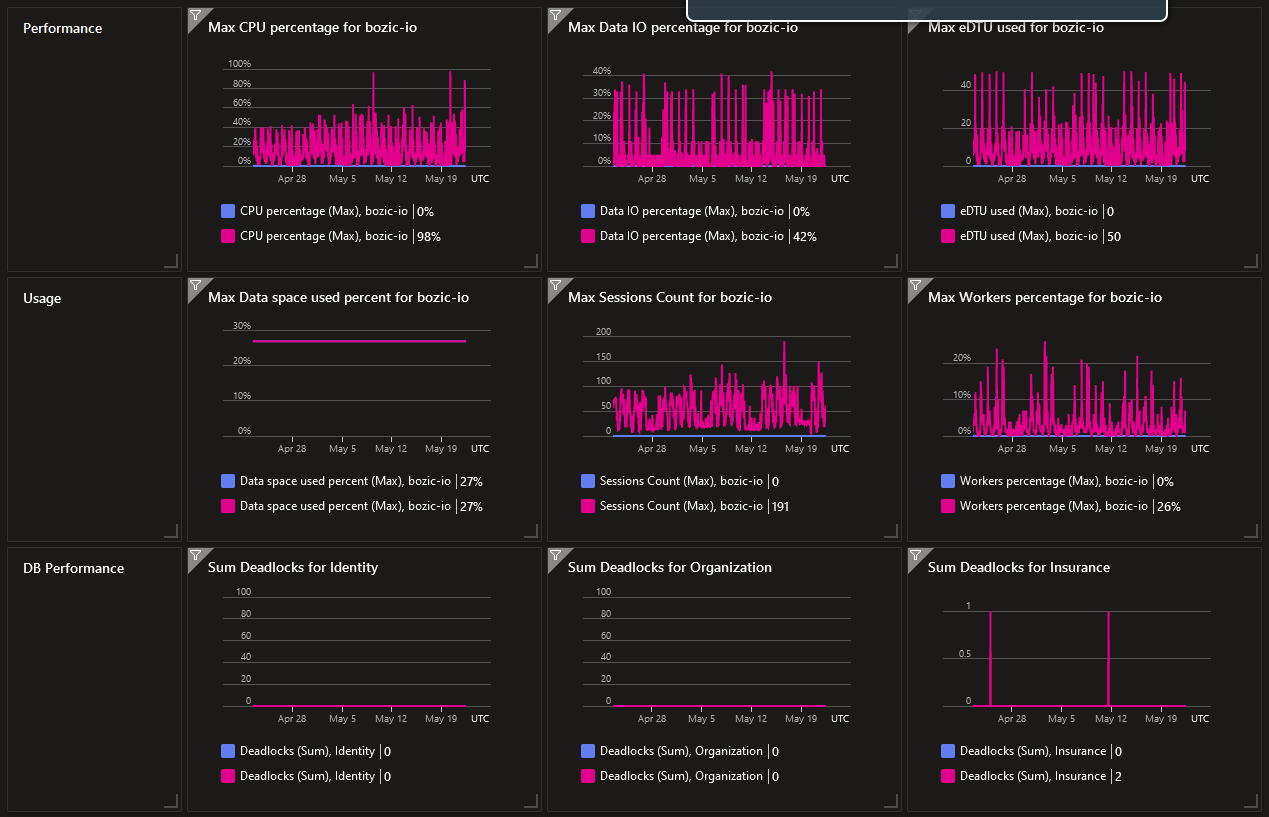 Figure 13. LIA DB processing capacity
Figure 13. LIA DB processing capacity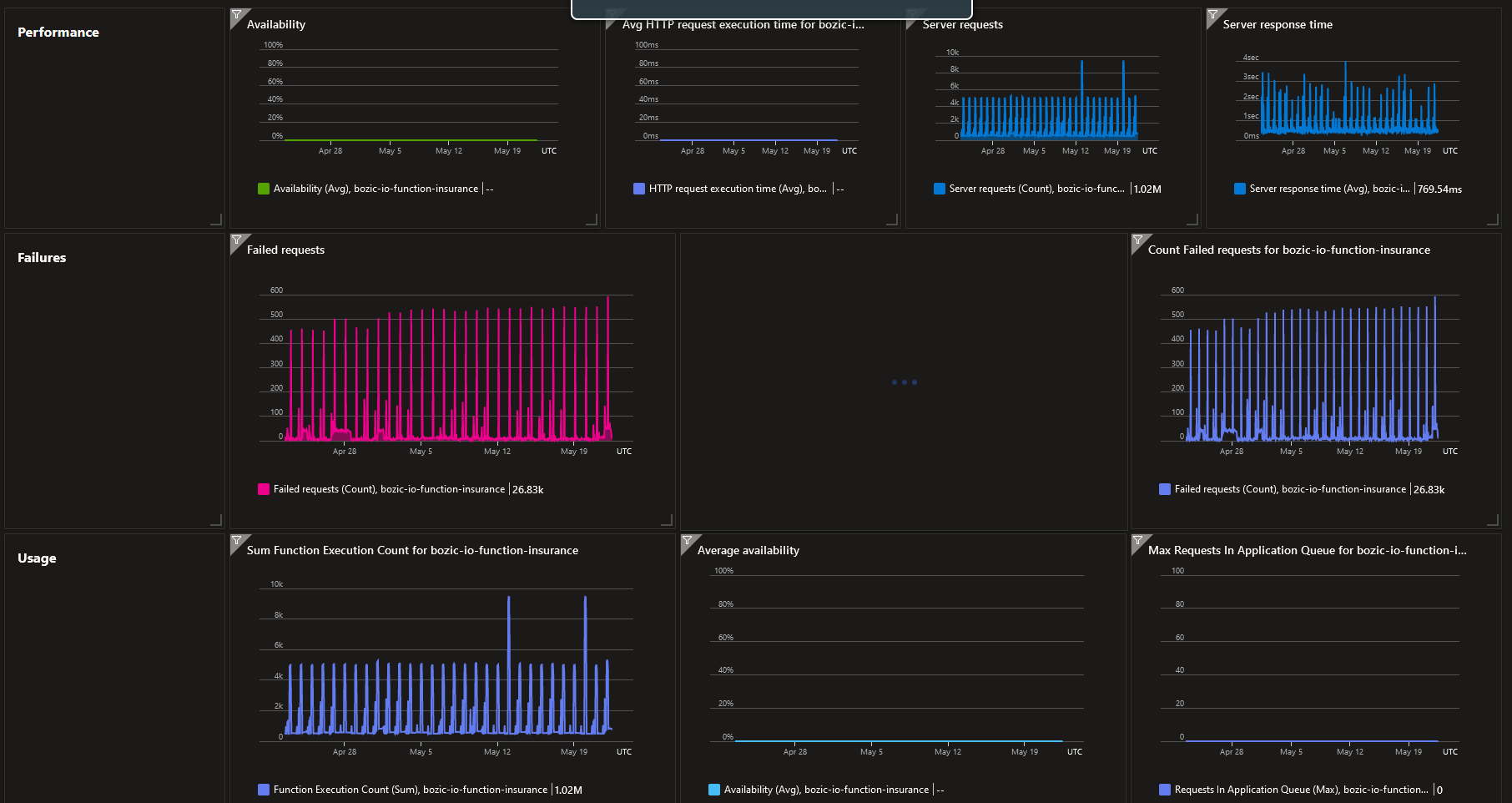 Figure 14. LIA Function processing capacity
Figure 14. LIA Function processing capacity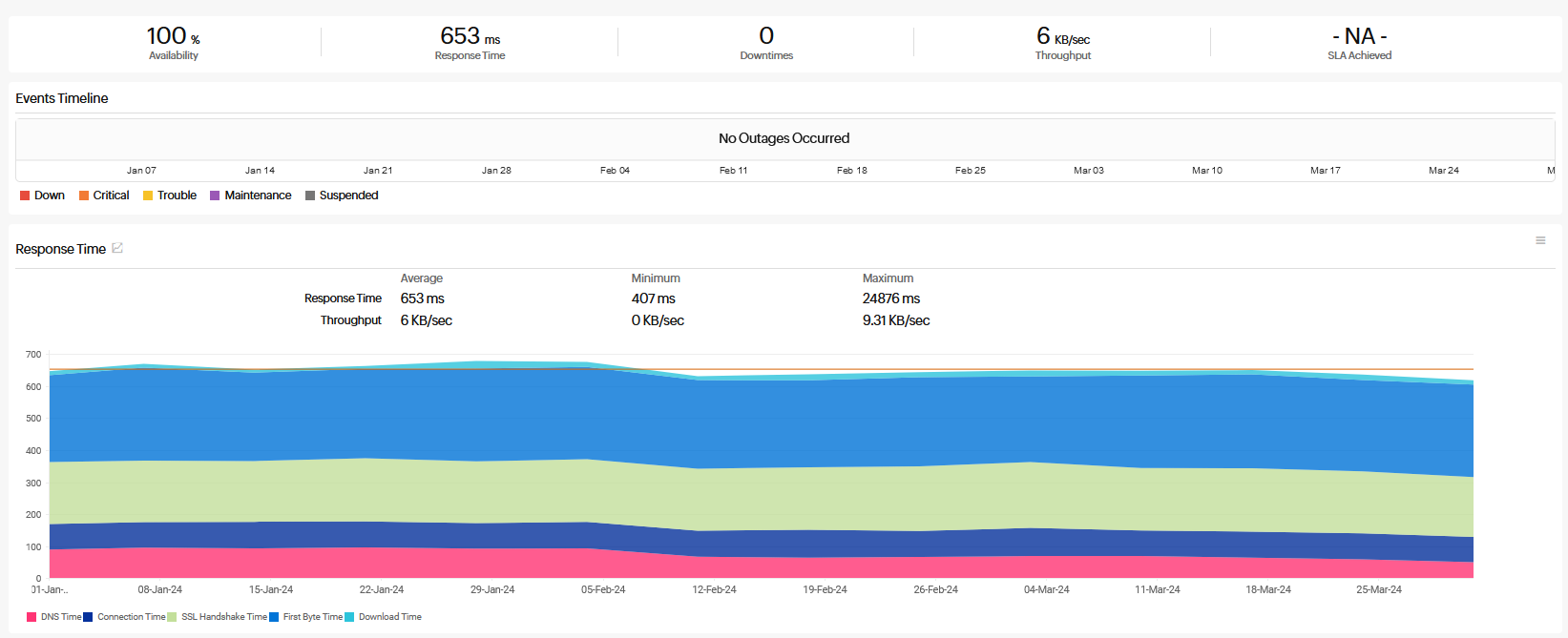 Figure 15. LIA availability
Figure 15. LIA availability -
AFBIS processing capacity not reviewed due to not being in production
-
Brisk processing capacity not reviewed due to not being in production
PII use review
-
Reviewed PII use
Raw PII access is limited to Marin Božić (marin@bozic.io) Luka Ferlež (luka.ferlez@bozic.io) ** LIA API web app
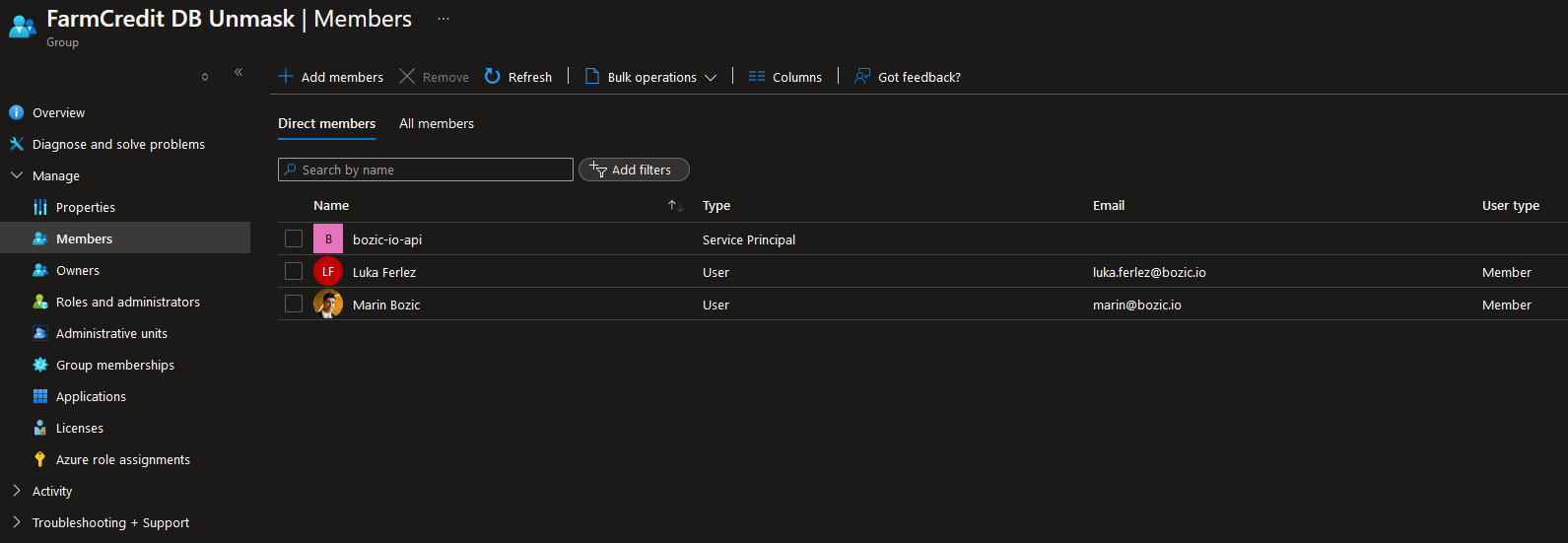 Figure 16. LIA Unmask group members
Figure 16. LIA Unmask group membersUnmask group is the only authorized to view masked PII
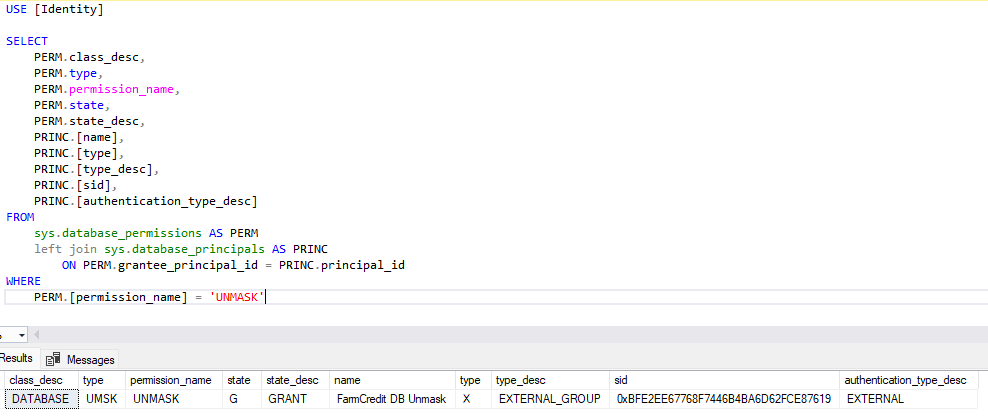 Figure 17. LIA Identity DB Unmask permissions
Figure 17. LIA Identity DB Unmask permissions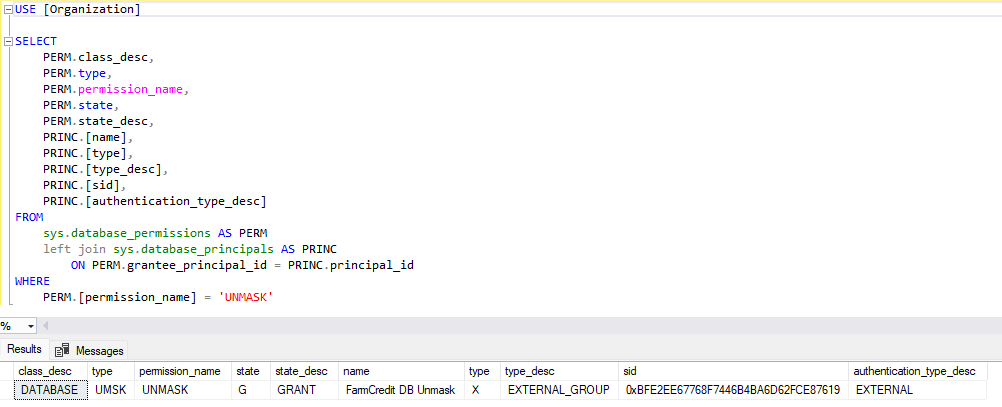 Figure 18. LIA Organization DB Unmask permissions
Figure 18. LIA Organization DB Unmask permissions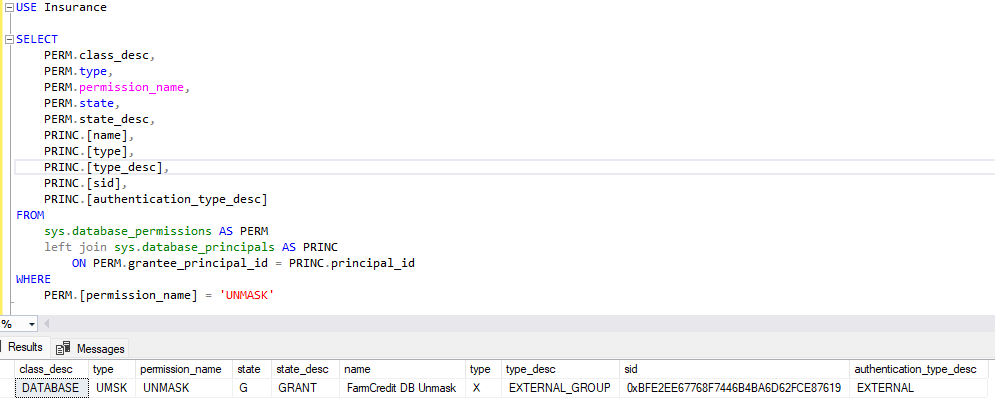 Figure 19. LIA Insurance DB Unmask permissions
Figure 19. LIA Insurance DB Unmask permissionsPII is used only the application system and is not exported or removed from the system.
Cybersecurity review
LIA
Penetration testing
System penetration & vulnerability scan is performed annually. The latest results have been obtained on 27th November 2023 from Appalachia technologies LLC, 5012 Lenker Street, Mechanicsburg, PA 17050.
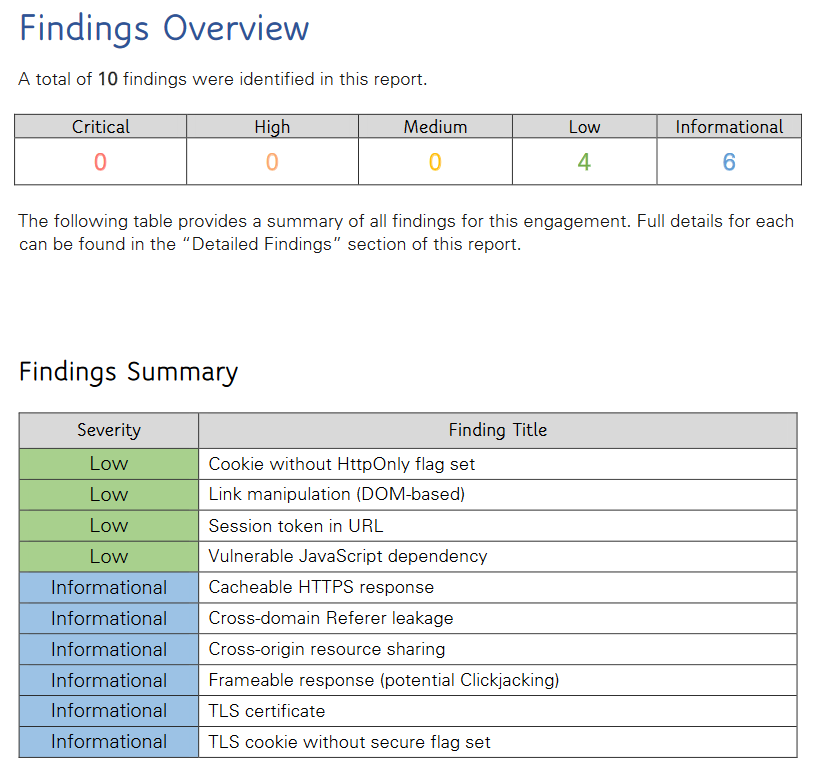
The penetration test results are deemed satisfactory. * Low findings are required the used OpenIDC protocol for authentication and do not pose a security risk * Informational findings are accepted
System exposure
-
Database
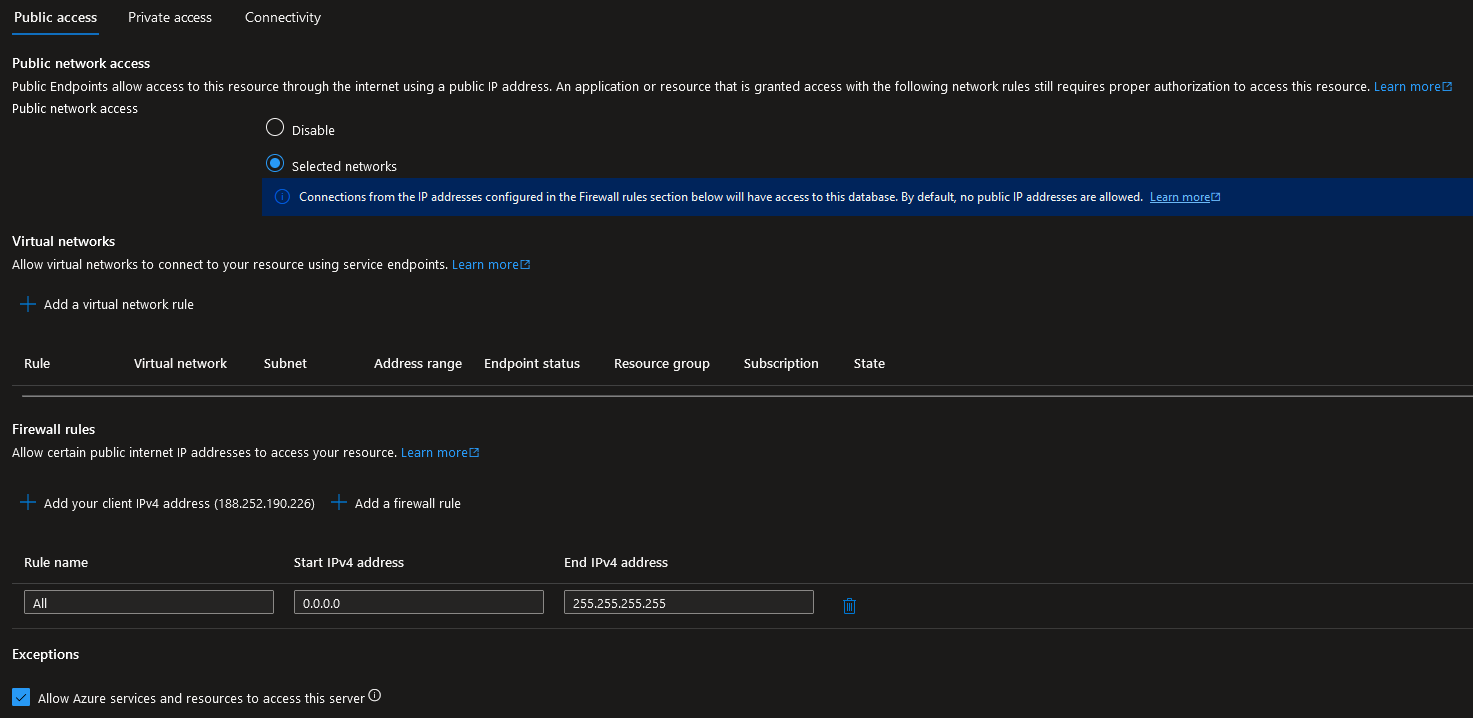 Figure 21. bozic-1 db server from public networks
Figure 21. bozic-1 db server from public networks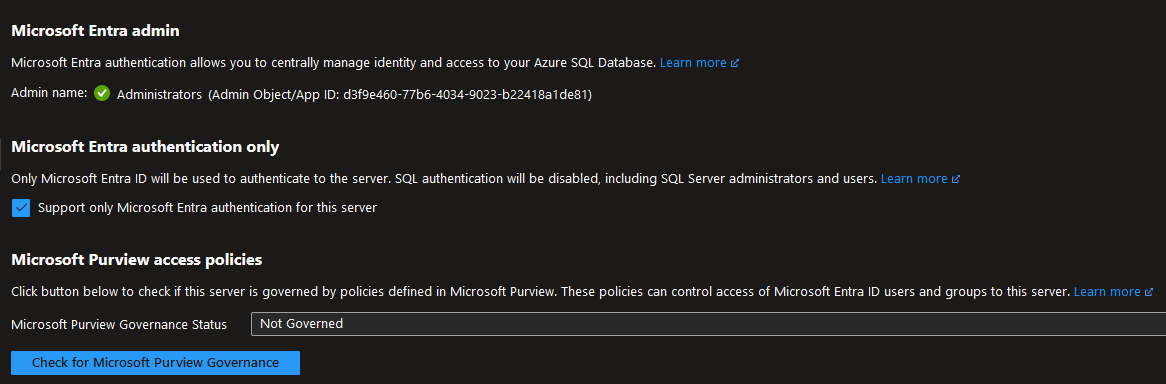 Figure 22. bozic-1 db server authentication settings
Figure 22. bozic-1 db server authentication settings Figure 23. bozic-2 db server from public networks
Figure 23. bozic-2 db server from public networks Figure 24. bozic-2 db server authentication settings
Figure 24. bozic-2 db server authentication settings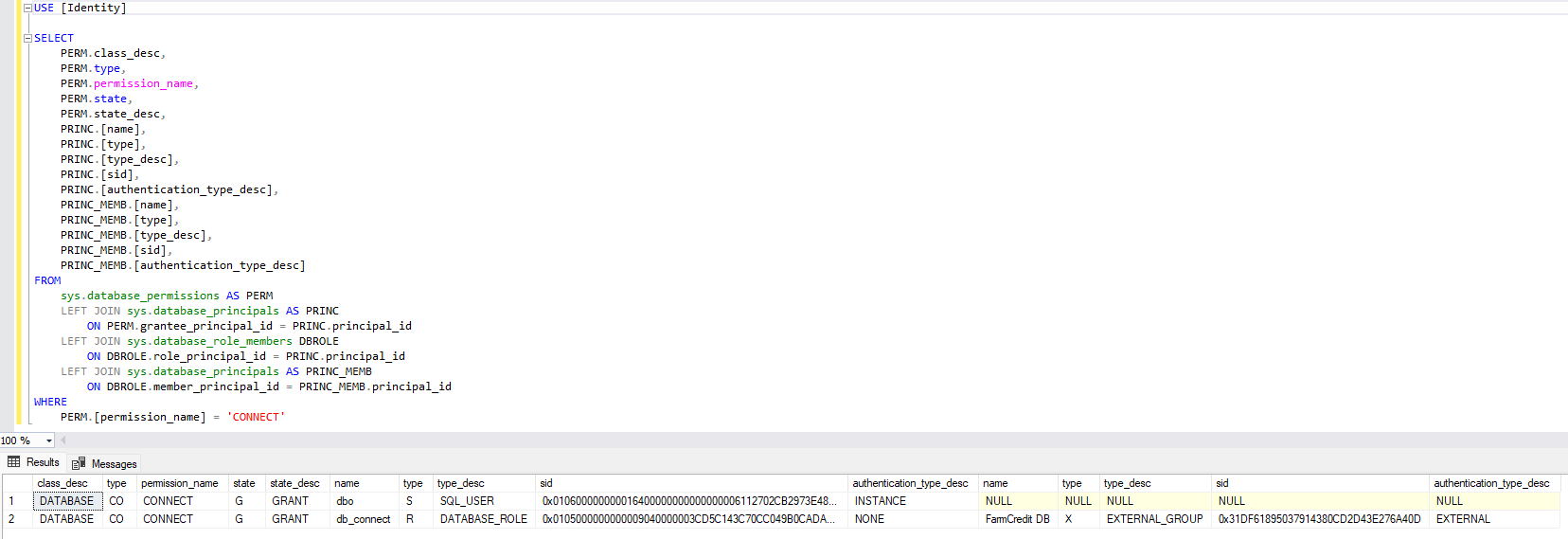 Figure 25. Identity connect privilege
Figure 25. Identity connect privilege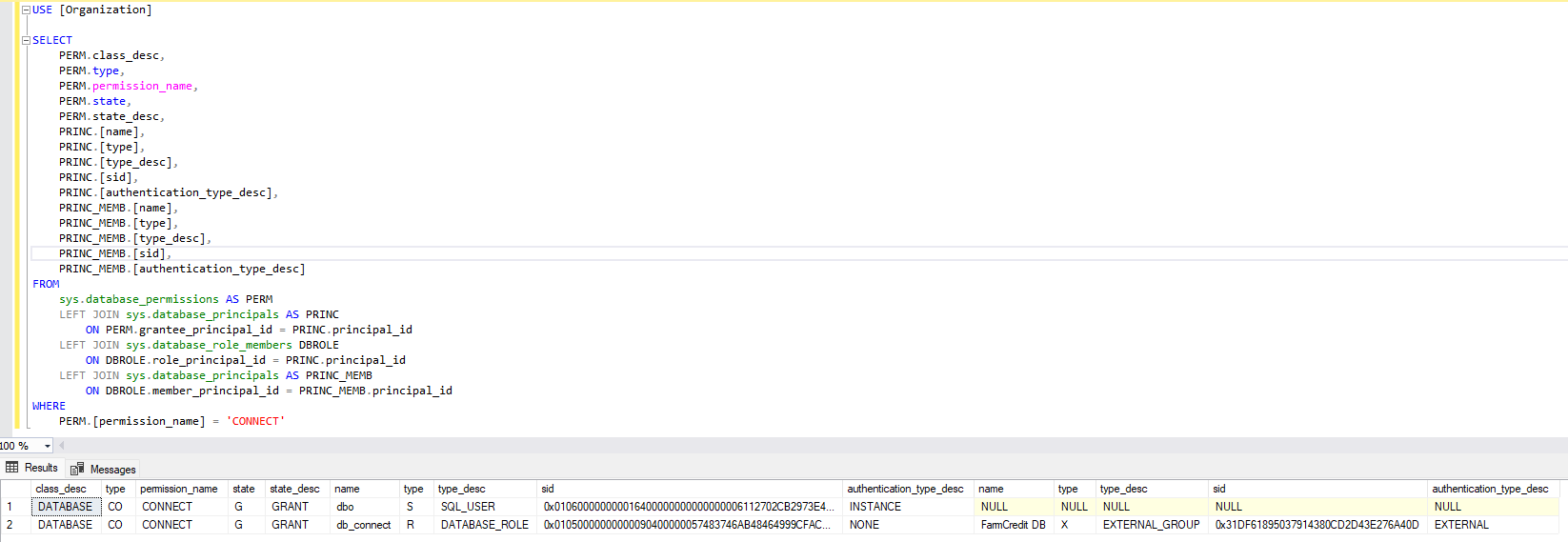 Figure 26. Organization connect privilege
Figure 26. Organization connect privilege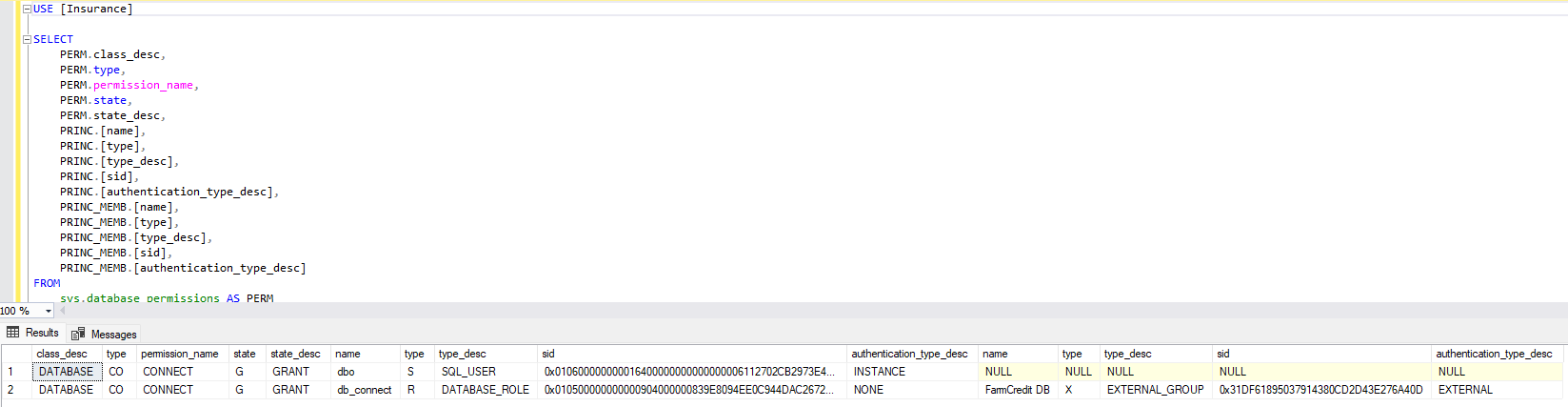 Figure 27. Insurance connect privilege
Figure 27. Insurance connect privilege-
Database servers are available for connection through public networks
-
Connection to the servers is possible only using Entry ID
-
Connection to the servers is possible only for users in FarmCredit domain group
Database server exposure is minimal, however should be tightened as there is no business need for public network access.
-
Storage
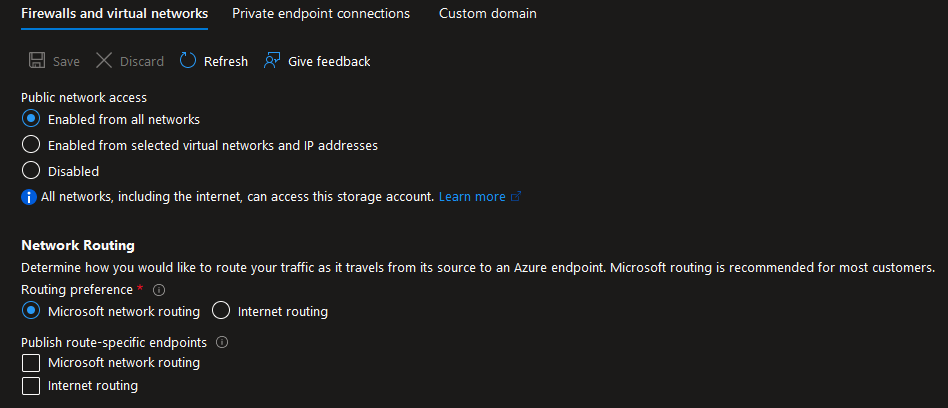
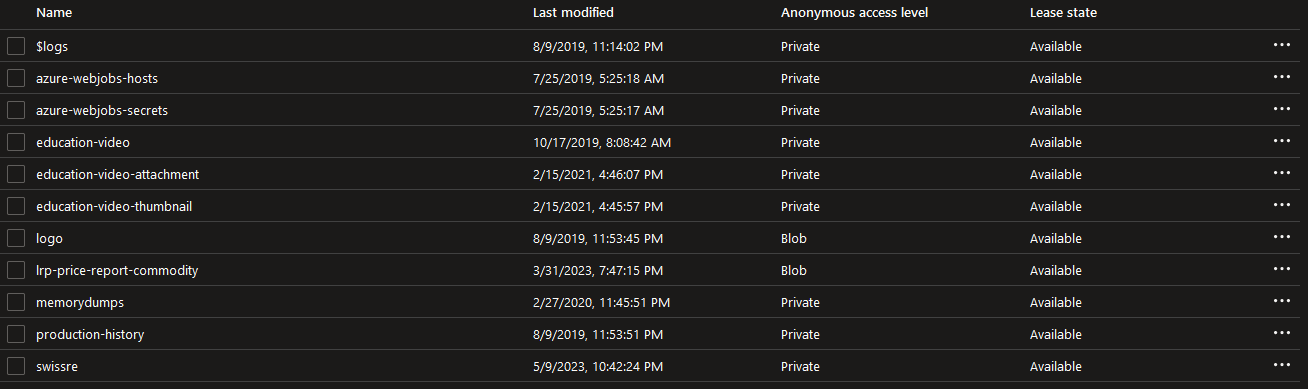
-
Access from public networks to storage account bozicio is enabled.
-
Container access is set to private with the exception of "logo" & "lrp-price-report-commodity" containers
Public unauthenticated access is possible only to containers "logo" & "lrp-price-report-commodity" which contain information & documents that are required to be publicly available.
AFBIS
AFBIS system is under development, no penetration testing has been conducted
Brisk
Brisk system is under development, no penetration testing has been conducted.
Actions
-
Expand data masking
Database contain additional potentially sensitive data and should be masked where ever such data is included. All personal names, usernames, address, phone numbers and similar personal data should be masked in all databases.
Database that contain such data and it is not masked are the be corrected
-
LIA Insurance @maja.pilipovic
-
AFBIS Quoter @tea.milicevic
-
Brisk Quoter @hana.ercegovac
-
-
Resolve causes of failed daily functions in LIA @maja.pilipovic
-
Advise AFBIS of the need to conduct penetration testing on the AFBIS system prior to going to production @tea.milicevic
-
Remove access to Database servers from all networks and enforce Private endpoint connections only @maja.pilipovic